Cybersecurity and Data Protection
System integrity check
Prevent unauthorized interference with your VMS
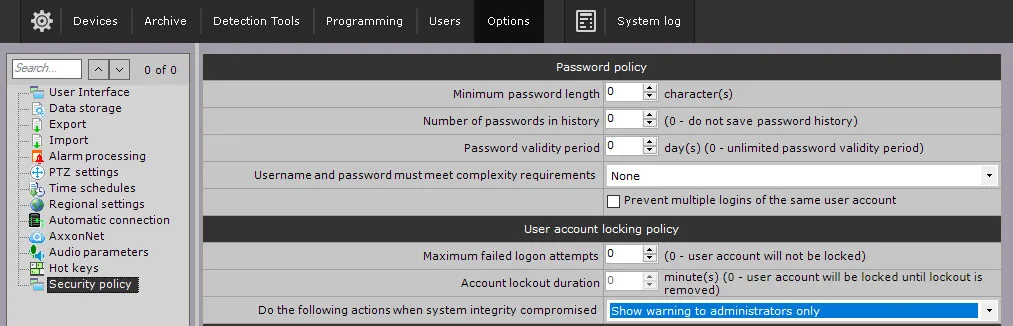
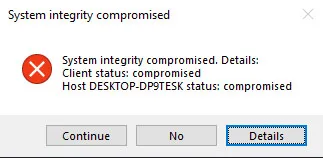
Ensure the security of your video management software (VMS) with robust cybersecurity measures, including data encryption. Axxon One prioritizes system integrity to prevent unauthorized interference in your VMS operations. When you start servers and clients, our software automatically checks the digital signature for all executable files. If all files are in place and match their signatures, a “System integrity check passed successfully” record appears in the system log.
Otherwise, a “System integrity check failed” event is registered, and you can set the system to perform one of the pre-configured actions:
- Show warning to administrators.
- Show warning to all users.
- Block users without admin rights.
- Stop non-vital services.
Security policy
Protect your VMS from unauthorized access
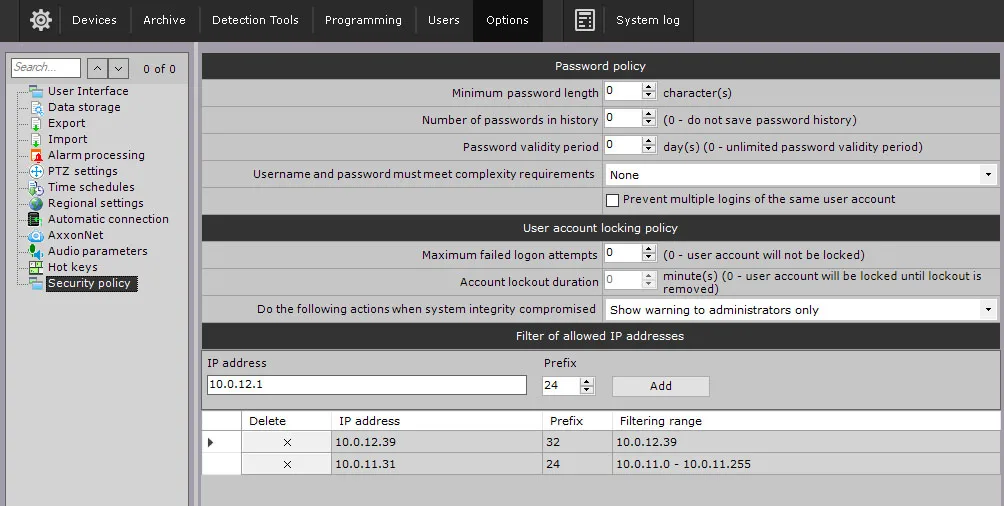
Axxon One security policy ensures that no unauthorized persons can access the system. The user security policy includes:
- Setting a minimum password length.
- Setting the password validity period and the number of passwords in history.
- Checking the password strength.
- Prevention of multiple simultaneous sessions.
- Blocking the user and specifying the ban time/number of failed login attempts.
- Setting a range of permissible IP addresses for client computers.
- Setting access to the server with administrator confirmation.
Each user-related event includes the user’s IP address, and the Export Start event contains the username. When accessing the server, the MAC address of the client computer is registered in the system event log.
Cloud cybersecurity features
Secure connection and password storage
Enhance security with our cloud cybersecurity features, including secure connection and two-factor authentication. Your data’s confidentiality is maintained through data encryption.
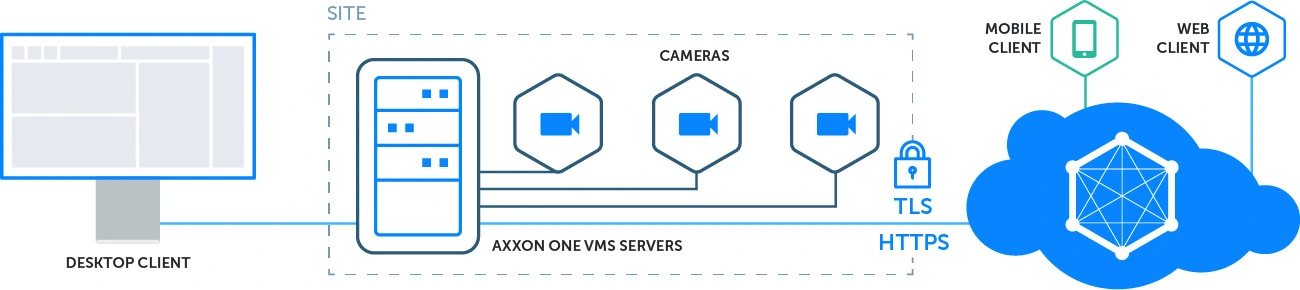
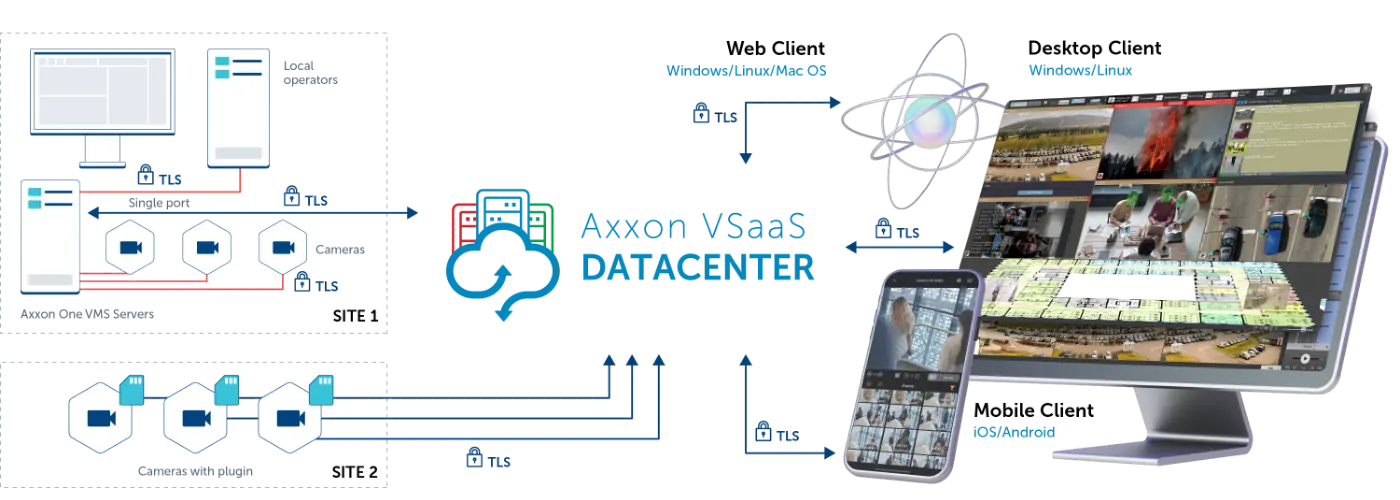
AxxonNet cloud service connects to your Axxon One VMS servers via the HTTPS protocol using TLS encryption. No opening any ports or deploying other potentially vulnerable settings is needed, which ensures that your VMS does not become externally accessible. Transmitted video and other data are encrypted, which makes it impossible for unauthorized persons to access your information.
In AxxonNet, no user passwords are stored unencrypted (as cleartext), but password hashing is applied instead. When you enter your credentials to register in AxxonNet, the password is processed with a hashing algorithm, and only the hash sum is stored. When you enter your password to log in, the algorithm calculates its hash sum and compares it to the stored one to grant you access to the service. It is impossible to reconstruct a password based on the hash sum, so your vital data is inaccessible to attackers.
End-to-End Secure Connections
Encrypted video streaming
Axxon One guarantees secure end-to-end connections through the implementation of the HTTPS protocol, ensuring that transmitted data is protected with TLS encryption. It supports secure camera connections to both on-premises and cloud-based Axxon One VMS servers. The desktop client establishes a connection to the server via a single port, aligning with corporate security policies.
Related Resources
Ознайомтеся з вичерпними технічними характеристиками програмного забезпечення Axxon One VMS, включаючи основні функції, спеціальні функції, відеоаналітику, а також підтримувані пристрої та стандарти.
Завантажте PDF-версію повної презентації Axxon One, що містить детальну інформацію про наше сучасне програмне забезпечення для керування відео.
Отримайте доступ до загальної інформації про функції та технології Axxon One VMS у зручній формі.